The computers, tablets, and smartphones that you purchase today are bare. They do not come with the needed Internet and Firewall security protection software installed. You will need to buy and install good Internet security, firewall, anti-virus, anti-spyware, anti-spam, and privacy-protection software to protect you from Hackers and Cyber criminals.
Once these products are installed and setup on your computer system, it is extremely important that you download and install security updates on a regular basis. In addition, you should install security fixes, patches, and updates to your operating system and office management software, as well as, any software product that you use frequently. Basically, keep your software up-to-date. All of these products have automatic update and install capability. So just turn these settings on.
Even with all of the above software properly installed and setup, you still need to take additional steps and precautions when using your computer and the Internet. These steps and precautions will be just as important in protecting yourself from phishing, spammers, RATs, Trojans, malware, spybots, keybots, keyloggers, spyware, hackers, viruses, “social engineers”, and identity theft. Here are some things that you should be conscious of every time you use your computer or the Internet:
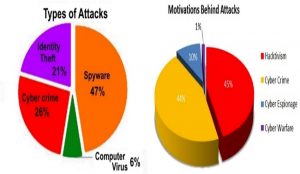
- Identity theft and fraud are the two most serious problems facing the Internet.
‘ - Cyber crime is increasing at a very rapid pace.
‘ - International cyber criminals are growing in numbers.
‘ - Fraud and identity theft are not new, but the Internet is making it accessible to more criminals.
‘ - These criminals are becoming ever more sophisticated.
‘ -
Computer-based fraudsters are finding new ways to trick people — not technology — to get the information they seek.
The “social engineering” nature of many of the recent attacks can only be resisted by educated users who are unwilling to fall for scams perpetrated by criminals “phishing” for personal data. Viruses, hackers, spammers, “phishing”, and spyware can all be dealt with using the above mentioned technology solutions. But technology alone cannot help someone who has decided to click on a link that appears to be part of a message from his/her bank, brokerage, credit card company, insurance company, financial services company, etc.—but really isn’t? The aforementioned type of companies will not ask you for personal information, usernames, or passwords via your e-mail address. E-mail is not a secure and trusted medium for communication and to transfer secure information. Please take the following steps and precautions to protect yourself and others:
- Be wary of e-mail. Never click on any link to a bank, brokerage, credit card company, insurance company, financial services company, eBay, or other online merchants. If you ever receive an email asking you to click on a link to change your username/password or to provide the sender with personal information, please ignore it and immediately flag it as junk mail. Then delete the message.
‘ - Nobody needs to verify your passwords. Ever.
‘ - Practice good computer hygiene. Don’t click on attachments.
‘ -
Run both anti-virus and anti-spyware applications. Firewall and privacy protection software should also be run. Update this software, as well as your operating system, on a regular basis.
‘ - If asked to call someone, use the listed telephone number and ask for that person’s extension. Criminals often give scam telephone numbers to intended victims. If you don’t know who’s asking, then there is no need to call them. It is usually a scam.
‘ - Order credit reports yearly and review them carefully.
‘ - Watch credit card and bank statements for small withdrawals. These are sometimes used to take small amounts of money that customers don’t consider to be worth reporting. But 10 cents a month from 100,000 accounts really adds up.
‘ - Encrypt it or shred it. Use a cross-cut shredder (makes confetti, not long strips which are too easily reassembled) or burn documents containing personal information. Do not store PINs on your computer; lock them up or encrypt them.
‘ - Don’t provide (or offer) unnecessary information. Always ask yourself, “Why do these people need my information?”
If you follow these steps and precautions, you will avoid many of the scams and traps that criminals create to gather personal information which they then turn into cash. You will also help protect yourself against the accidental release of information, as well as against unscrupulous marketers and others.